Exposure Simulator
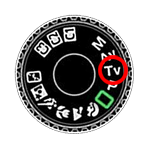
Exposure Simulator -3..2..1..|..1..2..3+ ↑ Shooting Mode: Shutter Priority Aperture Priority Manual Camera Settings: Note! The exposure portion of this simulator currently does NOT work with Internet Explorer! Please use Chrome or Firefox instead. This tool attempts to roughly simulate a final photograph given a particular set of camera settings. The simulation includes demonstrating depth-of-field based […]
Do not apologize for replying late to my email

by Ploum on 2026-02-11 You don’t need to apologize for taking hours, days, or years to reply to one of my emails. If we are not close collaborators, and if I didn’t explicitly tell you I was waiting for your answer within a specific timeframe, then please stop apologizing for replying late! This is a […]
Chrome extensions spying on 37M users’ browsing data

Summary We built an automated scanning pipeline that runs Chrome inside a Docker container, routes all traffic through a man‑in‑the‑middle (MITM) proxy, and watches for outbound requests that correlate with the length of the URLs we feed it. Using a leakage metric we flagged 287 Chrome extensions that exfiltrate browsing history. Those extensions collectively have […]
A Cosmic Miracle: A Remarkably Luminous Galaxy at z=14.44 Confirmed with JWST
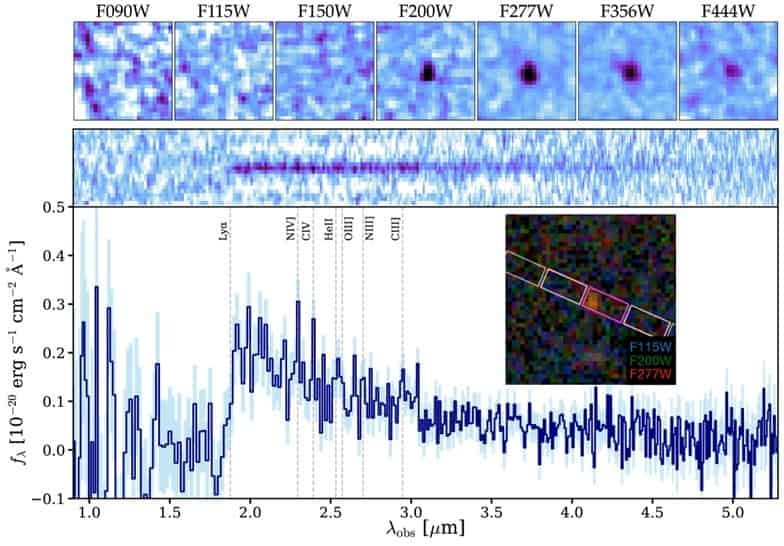
Naidu, Rohan P., Pascal A. Oesch, Gabriel Brammer, Andrea Weibel, Yijia Li, Jorryt Matthee, John Chisolm, et al. 2026. “A Cosmic Miracle: A Remarkably Luminous Galaxy at zspec = 14.44 Confirmed with JWST.” The Open Journal of Astrophysics 9 (January). https://doi.org/10.33232/001c.156033.
The Day the Telnet Died

A long, long time ago I can still remember how a protocol used to make me smile And I knew if I had my chance That I could make those botnets dance And maybe they’d be happy for a while But January made me shiver With every packet I tried to deliver Bad news on […]
The Singularity will occur on a Tuesday
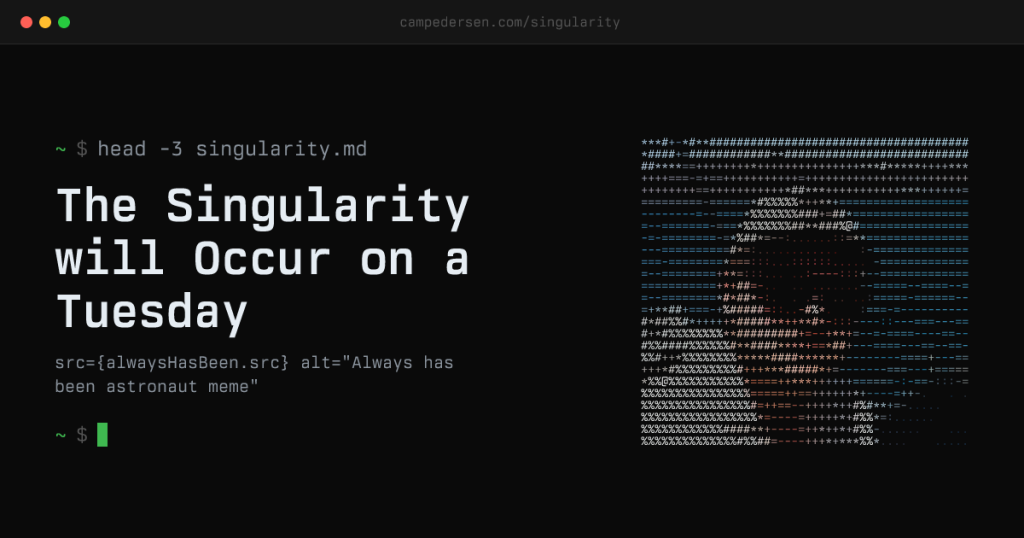
”Wait, the singularity is just humans freaking out?” ”Always has been.” Everyone in San Francisco is talking about the singularity. At dinner parties, at coffee shops, at the OpenClaw meetup where Ashton Kutcher showed up for some reason. The conversations all have the same shape: someone says it’s coming, someone says it’s hype, and nobody […]
Clean-room implementation of Half-Life 2 on the Quake 1 engine
Loading… Why am I seeing this? You are seeing this because the administrator of this website has set up Anubis to protect the server against the scourge of AI companies aggressively scraping websites. This can and does cause downtime for the websites, which makes their resources inaccessible for everyone. Anubis is a compromise. Anubis uses […]
Show HN: AI agents play SimCity through a REST API
Exploring a Modern SMTPE 2110 Broadcast Truck
In October, my Dad and I got to go behind the scenes at two St. Louis Blues (NHL hockey) games, and observe the massive team effort involved in putting together a modern digital sports broadcast. I wanted to explore the timing and digital side of a modern SMPTE 2110 mobile unit, and my Dad has […]
GLM-OCR: Accurate × Fast × Comprehensive
👋 Join our WeChat and Discord community 📍 Use GLM-OCR’s API Model Introduction GLM-OCR is a multimodal OCR model for complex document understanding, built on the GLM-V encoder–decoder architecture. It introduces Multi-Token Prediction (MTP) loss and stable full-task reinforcement learning to improve training efficiency, recognition accuracy, and generalization. The model integrates the CogViT visual encoder […]