DARPA Project Reveals One Person Can Control Dozens of Robots

26 Jan 2025 4 min read Planet Flem/iStock This article is part of our exclusive IEEE Journal Watch series in partnership with IEEE Xplore. Swarms of autonomous robots are increasingly being tested and deployed in complex missions, yet a certain level of human oversight during these missions is still required. Which means a major question […]
Merlion: A Machine Learning Framework for Time Series Intelligence
Table of Contents Introduction Comparison with Related Libraries Installation Documentation Getting Started Anomaly Detection Forecasting Evaluation and Benchmarking Technical Report and Citing Merlion Introduction Merlion is a Python library for time series intelligence. It provides an end-to-end machine learning framework that includes loading and transforming data, building and training models, post-processing model outputs, and evaluating […]
Zelensky leaves White House after angry meeting

James WaterhouseUkraine correspondent in Kyiv Reuters The spilling over we saw in the Oval Office today reflected what’s at stake for Zelensky and his country. This is not just about minerals or money; it’s about making sure three years of bloody fighting hasn’t been for nothing. It’s about the future existence of Ukraine in the […]
Harold Cohen and Aaron – A 40-Year Collaboration (2016)

Harold Cohen was a pioneer in computer art, in algorithmic art, and in generative art; but as he told me one afternoon in 2010, he was first and foremost a painter. He was also an engineer whose work defined the first generation of computer-generated art. His system, AARON, is one of the longest-running, continually maintained […]
Enhancing Frame Detection with Retrieval Augmented Generation

Abstract:Recent advancements in Natural Language Processing have significantly improved the extraction of structured semantic representations from unstructured text, especially through Frame Semantic Role Labeling (FSRL). Despite this progress, the potential of Retrieval-Augmented Generation (RAG) models for frame detection remains under-explored. In this paper, we present the first RAG-based approach for frame detection called RCIF (Retrieve […]
Show HN: Globstar – Open-source static analysis toolkit
Hey HN! We’re Jai and Sanket, co-founders of DeepSource (YC W20). We’re open-sourcing Globstar (https://github.com/DeepSourceCorp/globstar), a static analysis toolkit that lets you easily write and run custom code quality and security checkers in YAML [1] or Go [2]. After 5+ years of building AST-based static analyzers that process millions of lines of code daily at […]
3,200% CPU Utilization

A while back my machine was so messed up that I could barely ssh onto it. 3,200% CPU utilization – all 32 cores on the host were fully utilized! Compare that to my last bug where it only used 1 core, 100% Fortunately, it was using Java 17 runtime which had thread dumps with CPU […]
Imec demonstrates electrical yield for 20nm lines High NA EUV single patterning
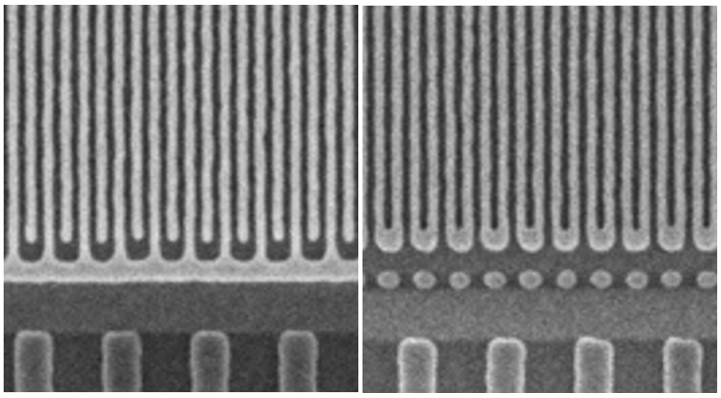
LEUVEN (Belgium), February 24, 2025— This week at SPIE Advanced Lithography + Patterning, imec, a world-leading research and innovation hub in nanoelectronics and digital technologies, presents the first electrical test (e-test) results obtained on 20nm pitch metal line structures patterned after single-exposure High NA EUV lithography. Measurements on both serpentine and fork-fork metallized structures show […]
Violence alters human genes for generations, researchers discover

Mulligan worked with Rana Dajani, Ph.D., a molecular biologist at Hashemite University in Jordan, and anthropologist Catherine Panter-Brick, Ph.D., of Yale University, to conduct the unique study. The research relied on following three generations of Syrian immigrants to the country. Some families had lived through the Hama attack before fleeing to Jordan. Other families avoided […]
Another Conflict Between Privacy Laws and Age Authentication–Murphy v Confirm ID
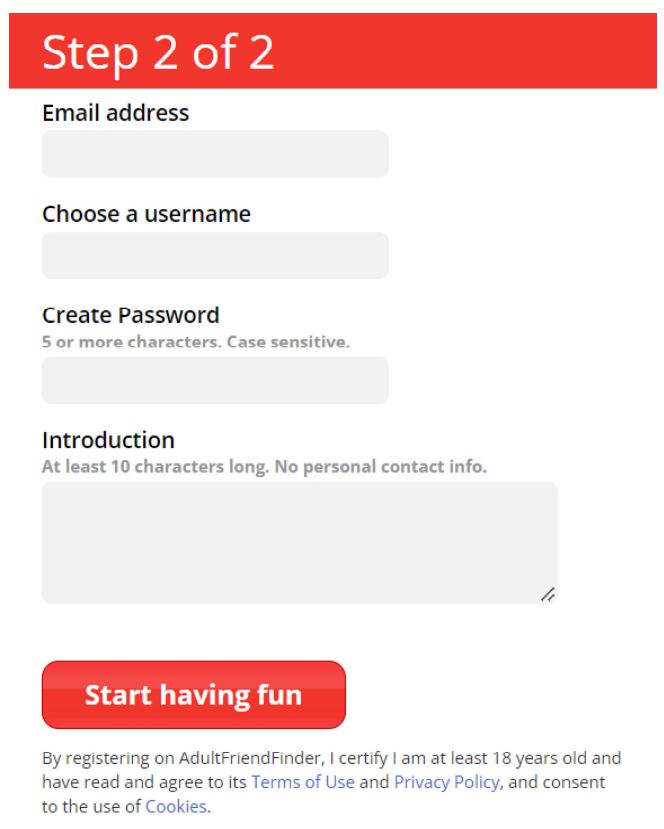
This opinion is a routine ruling over TOS formation and whether disputes must go to arbitration. However, before I dig into that question, I need to note the case’s chilling implications. * * * This case involves the Adult Friend Finder service (AFF), which age-authenticates its users. To do so, AFF required users to upload […]