The scientists fighting the epidemic of fraudulent science research

Nearly two decades ago, British anesthesiologist John Carlisle published an article on preventing postoperative nausea in the Cochrane Database of Systematic Reviews. Afterwards, however, Carlisle wasn’t celebrating his publication. Instead, he decided to look more closely at some of the papers included in his literature review. A staggering 68 of the 737 papers reviewed were […]
A brief history of the U.S. trying to add backdoors into encrypted data (2016)

A government agent uses an NSA IBM 360/85 console in 1971 (Photo: Wikimedia Commons/NSA). It’s been a weird week for America’s most valuable company—a firm whose tech products have such consumer goodwill they got away with forcing us to listen to U2—who is poised to go to court against its own government over its users’ right […]
Breaking Bitlocker – Bypassing the Windows Disk Encryption [video]
![breaking-bitlocker-–-bypassing-the-windows-disk-encryption-[video]](https://cdn-y.objects.dc-sto1.glesys.net/A1da965d3ac0f2e44c08f1ae072687d311/uploads/2024/02/391169-breaking-bitlocker-bypassing-the-windows-disk-encryption-video-1024x576.jpg)
How much bigger could Earth be before rockets wouldn’t work?

6 Answers
Low-Power Wi-Fi Extends Signals Up to 3 Kilometers

01 Feb 2024 3 min read Startup Morse Micro has used the HaLow standard to beam megabits of data across 3 kilometers using Wi-Fi. Morse Micro Most people have probably experienced the frustration of weak Wi-Fi signals. Even getting a network to cover every corner of a fairly modest house can be a challenge. That’s […]
Apple Vision Pro and ADHD
Apple Vision Pro reminds me that computers have become too efficient. I’m currently typing this blog post in a floating window in the middle of snow-covered Yosemite. I am a floating body manifested into the transcendental Tim Cook matrix. I look into the sky and follow the soft clouds as they pass overhead. They slowly […]
Show HN: Simple demo of a cold boot attack using a Raspberry Pi
{{ message }} This commit does not belong to any branch on this repository, and may belong to a fork outside of the repository. You can’t perform that action at this time.
Thou shalt follow these vintage computing commandments

Since vintage computing is supposed to be a spiritual experience, I point out that today, February 3, 2024, the Torah reading for this week is the Ten Commandments. Regardless of your religious tradition or lack thereof, I think we can all agree on these. Thou shalt check voltage and polarity on new-to-thee power supplies, or […]
The engineering behind Figma’s vector networks (2019)
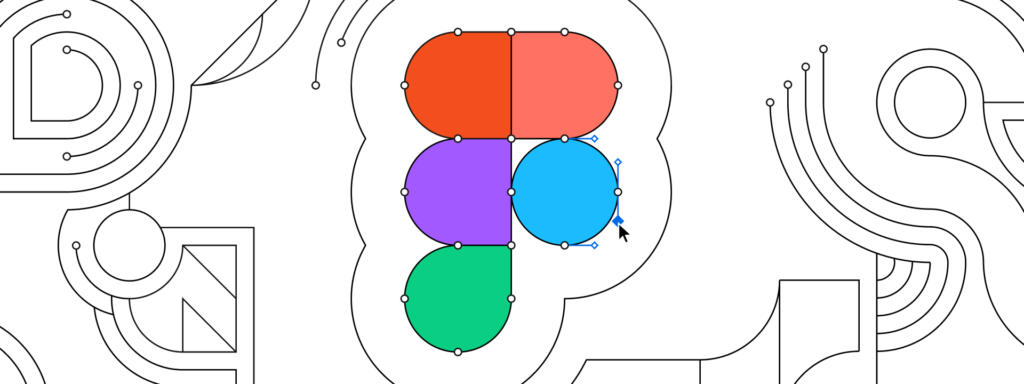
November 24, 2019 Adobe Illustrator introduced the pen tool back in 1987 as a tool for creating and modifying paths. Since then the pen tool has become incredibly widespread, so much so that is has become the de facto icon of the graphic design industry. The pen tool’s functionality hasn’t changed significantly in the 30 […]
Over the Edge – Microsoft’s Design Tactics Compromise Free Browser Choice [pdf]
Download PDF