Milwaukee reporter investigates cousin’s 1978 car bombing death

Florence Grady and Augie Palmisano reached the elevator doors at the same time. Both were tenants at Juneau Village Garden Apartments in downtown Milwaukee. And shortly before 9 a.m. that Friday — June 30, 1978 — both were heading to the basement of the apartment complex. Grady was carrying a basket of clothes to the […]
Law for Computer Scientists (2020)

by Mireille Hildebrandt This chapter first raises the question of what makes cybercrime ‘cyber’, followed by an introduction to international and supranational legal frameworks that are meant to cope with cybercrime. Finally, it will provide a more detailed analysis of the Cybercrime Convention.
New GitHub Copilot Research Finds ‘Downward Pressure on Code Quality’

News New GitHub Copilot Research Finds ‘Downward Pressure on Code Quality’ By David Ramel 01/25/2024 New research on the effect of AI-powered GitHub Copilot on software development cites some adverse results. The “Coding on Copilot” whitepaper from GitClear sought to investigate the quality and maintainability of AI-assisted code compared to what would have been written […]
Michael Lewis’s Blind Side

Michael Lewis is not interested in how or why people make mistakes. This might be surprising, given the subject matter of his latest book. Going Infinite chronicles the rapid ascent of cryptocurrency magnate Sam Bankman-Fried and the spectacular collapse of his crypto exchange FTX and hedge fund Alameda Research upon the revelation that he had […]
Show HN: Apple II clock using interrupts from physical pendulum clock
n TL;DR I made a clock for the Apple II, and used a pendulum clock and a sensor to drive it nn I was watching Dave Plummer’s video in which he made a clock in 6502 assembly for his Commodore PET. It looked like a fun thing to do on my Apple 2 Plus clone […]
Don’t Shave That Yak (2005)

The single best term I’ve learned this year. I want to give you the non-technical definition, and as is my wont, broaden it a bit. Yak Shaving is the last step of a series of steps that occurs when you find something you need to do. “I want to wax the car today.” “Oops, the […]
When the “R” goes missing from R&D (2021)

A Cautionary Tale about Too Much Siloing and Not Enough Trust Credit: Bob Cuthill via Getty Images I had my suspicions that something was terribly wrong with how our development team was organized, but I didn’t really put it all together until the day the Patent Attorney showed up. We had been working on a […]
Breaking SecuROM 7 – A Dissection
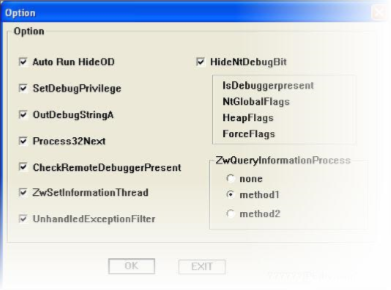
This is an archive of an old whitepaper made by three reverse engineering experts on breaking down SecuROM and its multiple layers of protection. Archive Opening Notes As mentioned, this is a whitepaper released by ARTeam in 2007/8, revealing how SecuROM 7 can be broken down using reverse engineering techniques. The tutorial is now around […]
I looked through attacks in my access logs
I’ve been self-hosting for over a decade. It’s freeing because I own my data, and do not depend on any platform other than my cloud host, which I can easily switch off. Self-hosting gives much insight into what it takes to run a cloud service. Anyone who’s had some practice doing this will likely tell […]
Rowhammer Resistant Coding in Sudo
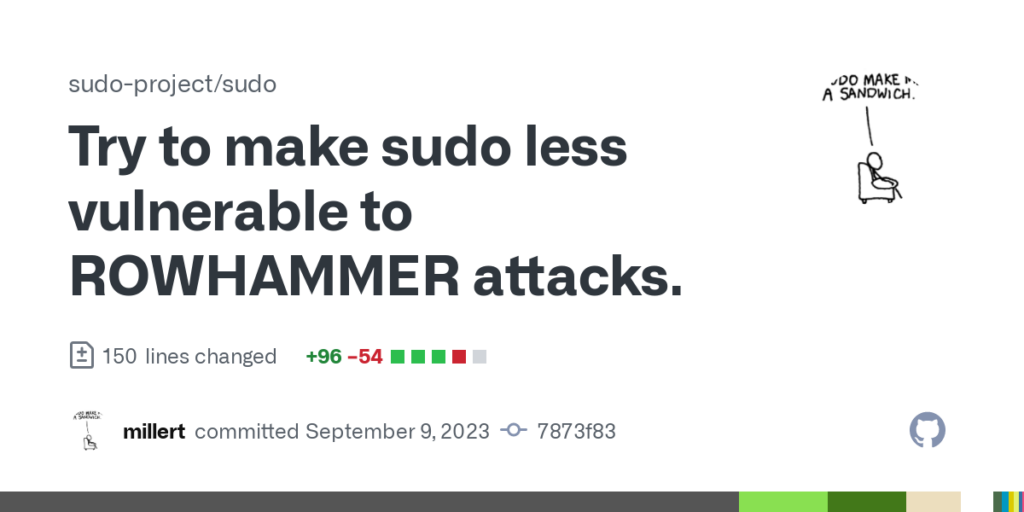
{{ message }} Commit Permalink This commit does not belong to any branch on this repository, and may belong to a fork outside of the repository. Browse files Browse the repository at this point in the history Try to make sudo less vulnerable to ROWHAMMER attacks. We now use ROWHAMMER-resistent values for ALLOW, DENY, AUTH_SUCCESS, […]